Many organizations enforce password policies to protect their user’s network & domain accounts. One credential that is often overlooked is the Unity Connection voicemail PIN, which can have costly consequences to your phone bill.
Cisco Unity Connection blocks this form of toll fraud out of the box unless you use a digit other than 9 for PSTN calls or have modified the default restriction tables to allow call handlers to transfer to external numbers.
It works as follows; the attacker calls into your auto-attendant and presses * to enter the voicemail sign-in. They then try to force their way into a voicemail box using simple PINs (1111, 1234, the extension of the box, etc.). Once successful, the attacker can set the Personal Call Transfer Rules to a long distance or international destination.
The Unity system is set up to bounce calls to costly destinations through your organization’s phone system. The attacker can now call back into the auto-attendant and dial the extension of the compromised voicemail box to get their call routed to their desired destination on your bill.
A similar fraud can also be achieved with the use of Alternate Contact Numbers when this option is enabled on a voicemail box.
There are a few ways to mitigate this:
Set the restriction tables correctly.
The two tables of interest here are:
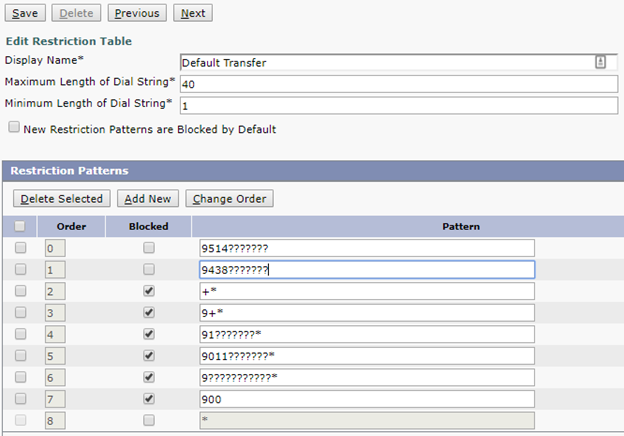
- Default Transfer; used to restrict what numbers users can set as a Personal Transfer rule or Alternate Contact Number via the phone interface.
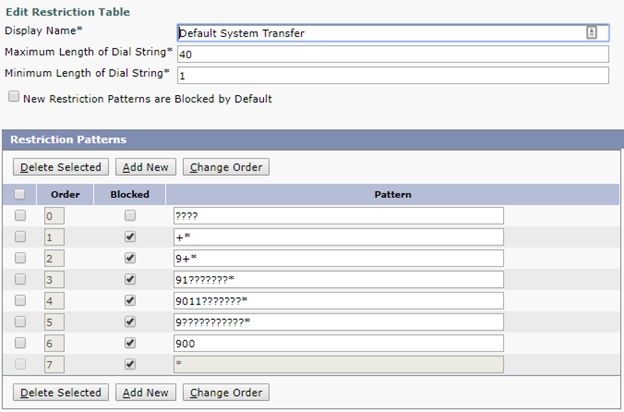
- Default System Transfer; used to restrict what numbers can be reached when dialing an extension in a Call Handler which has the option “Allow Transfers to Numbers Not Associated with Users or Call Handlers” enabled.
In a typical setup, Default System Transfer should block everything except for a pattern matching your extension length. This ensures no one can dial an external number directly in the auto-attendant.
For the Default Transfer table, if users should not be allowed to modify their own transfer rule or alternate contact numbers, block all PSTN patterns. Administrators can still set any number desired through the web interface as the restriction table is only checked when modifying the number via the TUI and not at the time the transfer takes place. If users should be allowed to modify these, try to be as restrictive as possible, allowing only local numbers is a good idea. However, if certain long distances numbers are required, restrict them to only the required area codes (91514??????? for example).
Proper CSS applied to the voicemail ports.
The voicemail port CSS applies to all calls out made from Unity Connection such as message notifications to mobile phones or transfers to dialed extensions from a Call Handler. Ensure that the line and device CSS pairing appropriately restricts calls down to only the number types it should be contacting (internal extensions and local calling for example)
Enforce password expiry and complexity.
A proper policy surrounding the user’s PIN will protect from attackers trying to brute force their way into the voicemail boxes. Short and trivial PINs are easily guessed and easy targets.
A non-trivial PIN is defined as follows by Cisco:
- The PIN cannot match the numeric representation of the first or last name of the user.
- The PIN cannot contain the primary extension or alternate extensions of the user.
- The PIN cannot contain the reverse of the primary extension or alternate extensions of the user.
- The PIN cannot contain groups of repeated digits, such as “408408” or “123123.”
- The PIN cannot contain only two different digits, such as “121212.”
- A digit cannot be used more than two times consecutively (for example, “28883”).
- The PIN cannot be an ascending or descending group of digits (for example, “012345” or “987654”).
- The PIN cannot contain a group of numbers that are dialed in a straight line on the keypad when the group of digits equals the minimum credential length that is allowed (for example, if 3 digits is allowed, the user could not use “123,” “456,” or “789” as a PIN).
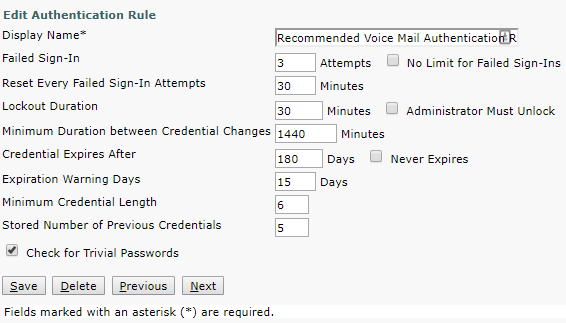
At a minimum, the voicemail authentication rule should have the “Check for Trivial Passwords” option enabled and expire the credential every six months. PIN length should also be at least six digits as it is only numerical. Other options, such as failed sign-in counts and lockout duration, are also good options to enable.
To read the Cisco tech note please click here.
Ready to take your unified communications from headache to hassle-free?
No throwing darts at proposals or contracts. No battling through the back-end. No nonsense, no run-around.