Early yesterday morning a collection of major vulnerabilities in most implementations of WPA2 was made public. The impact of this set of attacks, known as KRACK (Key Reinstallation Attack) is severe, allowing decryption of wireless traffic and, in some cases, traffic modification. You can find out more details on this attack at the website created by the discoverer and in the research paper Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2. Cisco is beginning to release updated firmware for their affected products. You can use this CERT page to find security updates from all the different impacted vendors.
What does this mean for your network?
Almost every wireless device is vulnerable to these attacks to some degree. For the issues known today the most severe impact is on wireless client devices. There are patches released and forthcoming for access points and controllers; you should apply these patches when they become available. However, we recommend that you focus your attention on client devices.
This table highlights the different issues and affected operating systems:
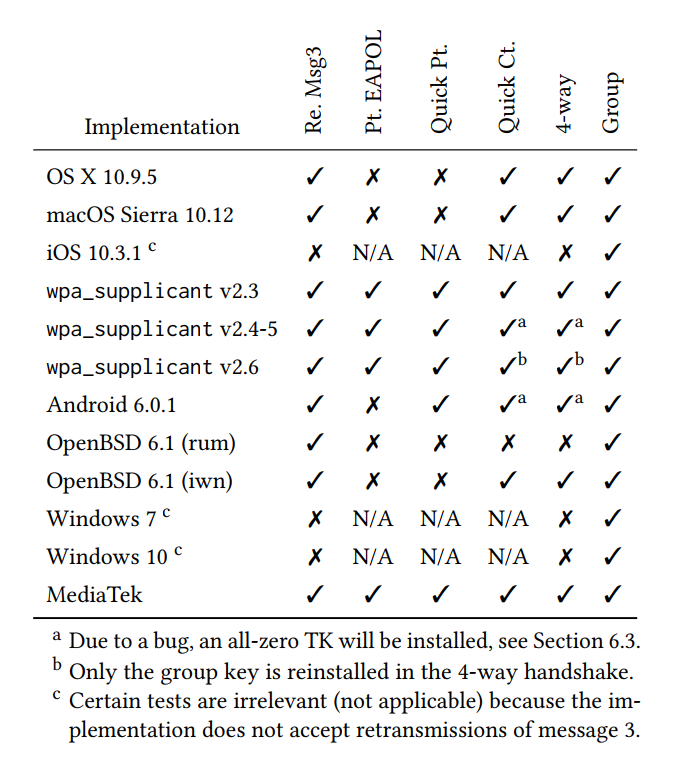
Table 1) Behaviour of clients: 2nd column shows whether retransmission of message 3 are accepted, 3rd whether plaintext EAPOL messages are accepted if a PTK is configured, 4th whether it accepts plaintext EAPOL messages if sent immediately after the first message 3, and 5th whether it is affected by the attack of Section 3.4. The last two columns denote if the client is vulnerable to a key reinstallation attack against the 4-way or group key handshake, respectively. Table credit Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2
From our perspective:
- Windows had a limited vulnerability to a small subset of the attacks that was addressed in the October security patches.
- MacOS is vulnerable to the attacks, updates are apparently in beta and will be released in the coming weeks.
- iOS has a limited vulnerability with a small impact, updates are apparently in beta and will be released in the coming weeks.
- Android devices are severely impacted by this issue.
Of these platforms, by far the most serious impact is on Android devices. The attack can trivially cause all traffic generated by a client device to be encrypted with a static key of all zeros making decryption trivial. Unfortunately, the release of security patches in the Android ecosystem remains extremely problematic except for the limited subset of devices that receive patches directly from Google. Pay close attention to security updates from your Android device manufacturer. Hopefully, they will release a fix for this issue.
Stay tuned; we will be updating this blog as further news is released.
Ready to take your unified communications from headache to hassle-free?
No throwing darts at proposals or contracts. No battling through the back-end. No nonsense, no run-around.