With the surge of emerging technologies, many companies are prone to getting the latest hardware and software they can get their hands on to improve their overall productivity and reduce costs.
However, one thing that is often neglected in this fast paced environment and that should be considered one of the most crucial aspect of a network’s infrastructure is its security. Being aware of technology vulnerabilities is the first step in avoiding the infiltration of any unwelcome and malicious intruders that could lead to a devastating aftermath.
This leads us to this very important topic: how to mitigate the risk of attacks on Cisco IOS SIP gateways.
In this post, we will review the following:
- How intruders would go about doing reconnaissance on a network in planning an attack,
- How to check if your device is prone to fingerprinting, and
- How to implement corrective measures to tighten-up these weak spots, making your Cisco network more secure.
1) How intruders would go about doing reconnaissance on a network in planning an attack
First, how would a hacker go about infiltrating your system. Well the first thing they would do to try to gain access to a network or device is reconnaissance. They would be looking for a probable door to the network. To do this, they would want to know the types and versions of all the devices that connect to the network this is also known as fingerprinting. Knowing this information could help them identify vulnerabilities that could then be exploited.
2) How to check if your device is prone to fingerprinting
Now let’s take a look at how you can check if your SIP gateway is prone to fingerprinting in your Cisco environment. In the following example, we used a tool called SIPsak (SIP swiss army knife) to test our environment. The test sent a simple OPTIONS message to a fictitious URI (sip:nobody@10.100.100.20) which the Cisco gateway then replied with a 200 OK, which indicates that this device is running IOS 15.2(4)M4. I don’t know about you, but seeing this detailed information is very unsettling as this information exposes a potential door to the network.
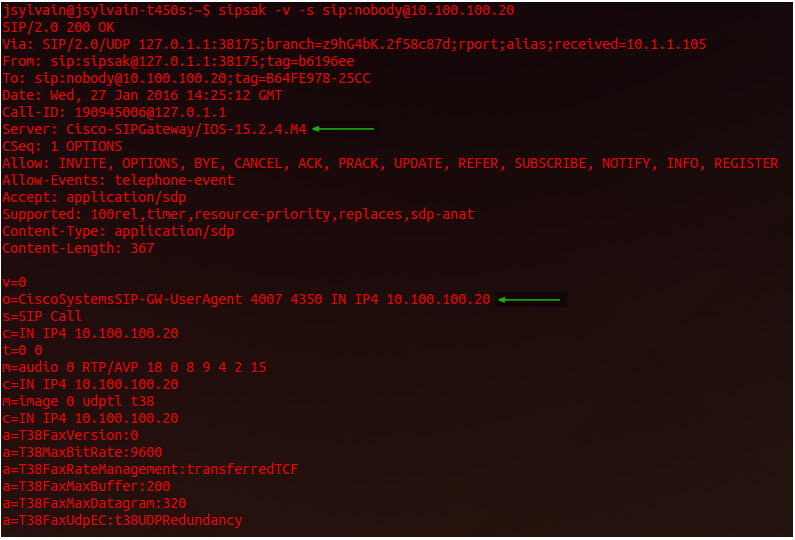
In the example above, we see 2 of the 4 fields in a SIP message that can provide information identifying the device as a Cisco device and provide the version right down to the build number for certain IOS versions:
- Server (server:)
- Session owner (o=)
- User agent (user-agent: )
- Cisco GUID (Cisco-GUID).
Visibility of this information obviously leaves your network at risk to unwelcome intruders. Fortunately, something can be done to change these settings and strengthen your overall Network security.
3) How to implement corrective measures to tighten-up these weak spots
These settings can be changed using SIP normalization rules of Cisco IOS. There are many ways to accomplish this. In our example, we have created 2 profiles to do so. The first one is the global profile where the server, session owner and user agent fields will need to be modified. The second is the outbound dial-peer facing profile where the same fields as above will need to be modified in addition to the Cisco GUID field. To create these modified profiles simply use the following commands in cli.
- Global profile
|
voice class sip-profiles 100 voice service voip |
- Outbound dial-peer facing profile
|
voice class sip-profiles 200 dial-peer voice X voip |
The <name> field is to be used with any desired nomenclature. For the purpose of this example, we have modified it to <VoiceGateway>, to allow up to see the results of these modifications. Now it is time to retest the system.
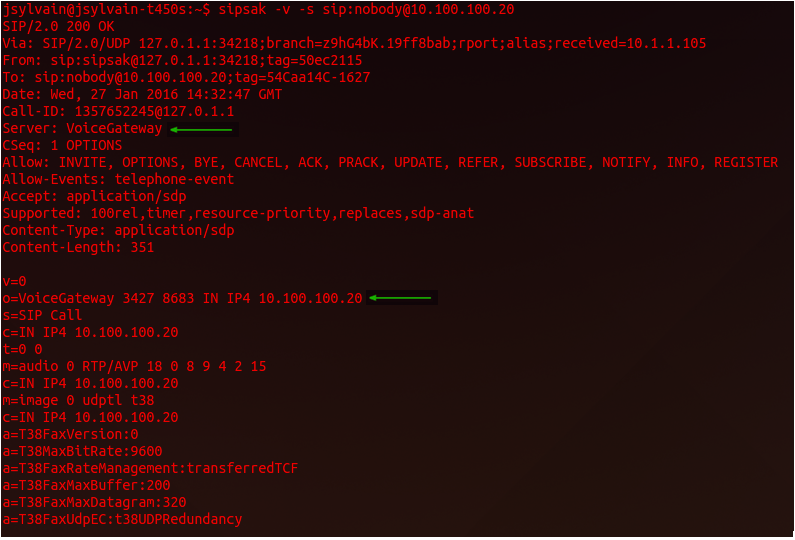
The results of this test show that the IOS version of the Cisco IOS devices is no longer being advertised. By doing this test and taking these corrective measures to restrict the divulged information, you will have increased the security of your Cisco Network environment.
Remember, this test alone does not replace normal security procedures that should always be in place, it simply reduces the risk of your Cisco IOS device from becoming a possible target.
Following the Cisco guide to harden Cisco IOS devices as well as the security portion of the Best practices when implementing SIP trunks for PSTN access should not be neglected while configuring your SIP gateways.
Have questions about the strength of your Cisco Network’s security and want some advice on network and security solutions? Give our experts a call and we will be happy to discuss any issues with you and see how we can help.
Ready to take your unified communications from headache to hassle-free?
No throwing darts at proposals or contracts. No battling through the back-end. No nonsense, no run-around.