Cisco WebEx Plugin Vulnerabilities Affecting Chrome, Firefox and Internet Explorer (CVE-2017-3823)
There is a severe bug in the WebEx extensions for Chrome, Firefox and Internet Explorer (CVE-2017-3823) that enables an attacker to execute arbitrary code on a machine if a user with the plugin installed visits a hostile website. A trusted website may also contain a hostile ad or XSS vulnerability that can be leveraged in this attack. This plugin is installed on approximately 10 – 20 million user machines.
Cisco has released an updated version of the plugin for Chrome and Firefox that reduces the risk of the of attack. With the updated version users are prompted if they want to join a WebEx meeting when a non-WebEx domain attempts to use the plugin. While this fix depends on users not accepting meeting prompts it’s a substantial improvement over the current behavior.
Google Bug Page: https://bugs.chromium.org/p/project-zero/issues/detail?id=1096
Cisco Security Advisory: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20170124-webex
Updating the Chrome Extension
Step 1: Exit Chrome completely including exiting Chrome from the system tray if present and start it. Start Chrome and Navigate to Settings > Extensions, confirm that at least version 1.0.5 is installed. Below you see the Extension screen with version 1.0.1 still installed after a restart.
.png)
Step 2: If it is not, you can enable developer mode using the checkbox in the upper right.
.png)
Step 3: There will then be a button to update extensions to the current version.
.png)
Step 4: After the update, you should be running version 1.0.5 or greater.
Updating the Firefox Extension
Step 1: Restart Firefox completely. Vulnerable versions of the Firefox plugin should already be blocked by Mozilla so at this point you should be safe.
Step 2: To validate that the plugin is up to date navigate to Add-Ons > Extensions. If you are not running version 1.0.3 then right click on the WebEx extension and select Find Updates to update it.
Internet Explorer
No fix has been released yet. We recommend that you disable WebEx plugins until a fix is announced. You should disable all plugins appearing in the “Cisco WebEx” section of Manage Addons in Internet Explorer.
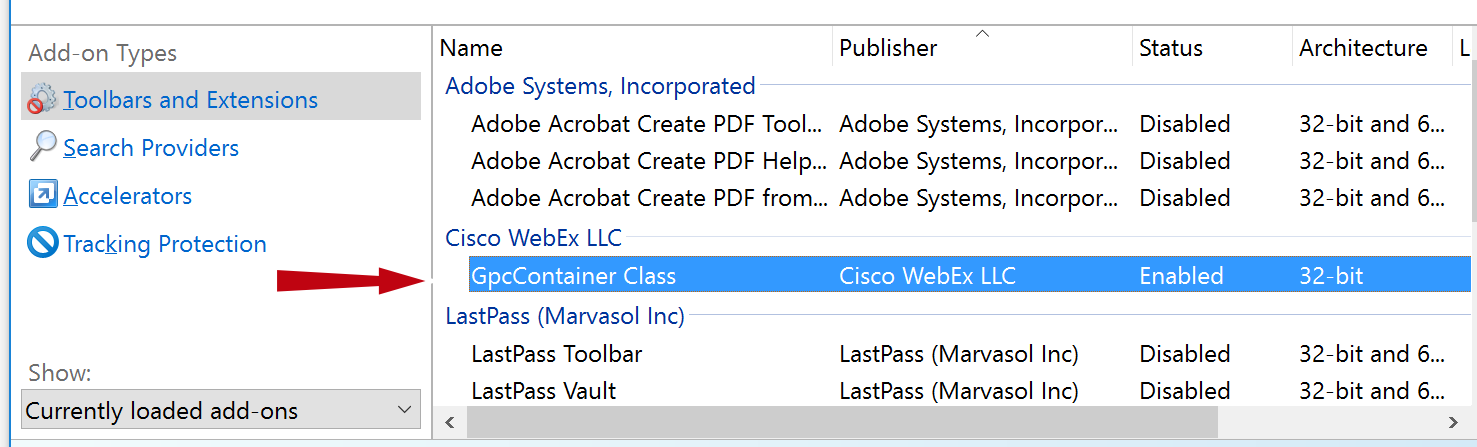
Unfortunately, this may prevent the user from connecting to WebEx meetings using Internet Explorer. However, they can use an alternative browser until a fix is made available. You could also consider our network mitigation approach discussed below.
Network Level Mitigation
Using an IPS or Next Generation firewall, you can block URIs containing the string
“cwcsf-nativemsg-iframe-43c85c0d-d633-af5e-c056-32dc7efc570b.html” that aren’t hosted on *.webex.com.
By only allowing the URI to be used on specific subdomains of webex.com, for instance, “yourcompany.webex.com” and other trusted vendors and partners (e.g. stack8.webex.com) could further reduce your risk and exposure. Even with the current version of the plugin, this solution will prevent users from accepting hostile meeting requests from untrusted websites and potentially hostile WebEx subdomains.
If you have any questions about how to properly secure your environment against this or other threats, please don’t hesitate to contact the team at Stack8
Ready to take your unified communications from headache to hassle-free?
No throwing darts at proposals or contracts. No battling through the back-end. No nonsense, no run-around.



