Cisco Jabber certificate validation helps establish secure connections with servers. Public CA-Signed Certificates are required for multiple platforms.
With Jabber, you can access presence, instant messaging (IM), voice, video, voice messaging, desktop sharing, and conferencing instantly, giving you and your team the freedom to be productive from anywhere, on any device.
1. Cisco Jabber certificate verification and validation
Why CA-Signed Certificates?
Cisco Jabber requires the use of certificate validation in order to establish secure connections with servers. Since Jabber is installed on multiple platforms, including Android and iPhone, CA-Signed certificates are required on all Cisco UC servers. CA-Signed certificates can also circumvent a Cisco Jabber certificate error.
Why not Wildcard Certificates?
Some companies may want to supply their own private key to the signing CA independently from CUCM or may request a wildcard cert. However, CUCM does not support the upload of a cert that the server itself has not generated the private key for (or that the hostname does not match in the case of *.cisco.com).
RHEL (Red Hat Enterprise Linux operating system) already supplies the means to do such import, but Cisco has not exposed those in the APIs or the Unified CM web pages.
There were requests for Cisco to devise a way to provide the ability for customers to generate wildcard certificates. However, Cisco did not approve such enhancements. CUCM 10.5 introduces a multi-server certificate feature, so one certificate can be used for the whole UCM cluster.
It is possible that using wildcard certs could make the Cisco Jabber certificate not valid.
For more information please read Bug #CSCta14114: Request for support of wildcard certificate in CUCM & private key import.
CA-Signed Certificates requirement for Jabber
Cisco Unified IM&Presence: HTTP (Tomcat - part of CUCM Multi-SAN), CUP-XMPP Cisco Unified Communications Manager: HTTP (Tomcat) Cisco Unity Connection: HTTP (Tomcat) Expressway Core and Edge HTTP (Tomcat)*
* Expressway certificates are requirements for Jabber MRA (Mobile and Remote Access feature).
Verify if a Certificate is Self-Signed or CA-Signed
The first step is to verify the type of certificates that are running on your server, in case you are not certain.
- Navigate to Cisco Unified OS Administration.
- Choose Security > Certificate Management.
- Look for tomcat certificates, or in the case of IM&P server, look for cup-xmpp certificates.
- Verify the Type (must be CA-signed and not Self-signed), and Issued By are the name of CA trusted.
Validating your CUCM Server list and UC services
If you still receive a Certificate Warning during the initial Jabber start-up after signing all required certificates and uploading them to the UC servers, you will need to verify a few configuration parameters.
- Go to CUCM CM Administration > System > Server list.
- Check that all your server nodes are defined with their Fully Qualified Domain Name (FQDN) and not with their IP address or their Hostname. This will be one of the reasons Cisco Jabber triggers the security warning.
- Make sure if you are changing this field from IP to FQDN, to schedule a maintenance window prior to the change.
- Verify all your Phones have a DNS reference assigned. Otherwise, they will not be able to register back to CUCM.
- Go to User management > User settings > UC Service.
- Verify the target for all UC services if you are using FQDN instead of IP or Hostnames.
2. Cisco Jabber certificate renewal process for Cisco Unified Communication Manager, Cisco Unified Communication IM and Presence, and Cisco Unity Connection
Public CA Certificate renewals
You can monitor your certificate’s expiration date through RTMT (Real-Time Monitoring Tool) alarms. Once the time is close to expiration, you need to renew your CA-Signed certs with your certificate provider. It is very important that you follow the same procedures again starting with the CSR creation to avoid a Cisco Jabber certificate error. Unfortunately, we have seen many clients trying to renew existing certificates without generating a new CSR from the UC server.
Example of RTMT alarm for certificate expiration:
-----Original Message-----
From: RTMT_Admin@company.com [mailto:RTMT_Admin@company.com]
Sent: October-15-17 8:00 PM
To: RTMT_Alarms <RTMT@company.com>
Subject: [RTMT-ALERT-CUCMCluster] SyslogSeverityMatchFound
At Sun Oct 15 19:00:17 CDT 2017 on node cucm.company.com, the following SyslogSeverityMatchFound events generated:
SeverityMatch : Critical
MatchedEvent : Oct 15 19:00:00 cucm local7 2 : 345: cucm.company.com: Oct 16 2017 12:00:00 AM.59 UTC : %UC_CERT-2-CertValidfor7days: %[Message=Certificate expiration Notification. Certificate name:tomcat.der Unit:tomcat Type:own-cert Expiration:Sat Oct 21 16:45:39:000 CDT][AppID=Cisco Certificate Monitor][ClusterID=][NodeID=cucm]: Alarm to indicate that Certificate has Expired or Expires in less than seven days AppID : Cisco Syslog Agent ClusterID :
NodeID : cucm
TimeStamp : Sun Oct 15 19:00:00 CDT 2017
SeverityMatch : Critical
MatchedEvent : Oct 15 19:00:00 cucm local7 2 : 346: cucm.company.com: Oct 16 2017 12:00:00 AM.60 UTC : %UC_CERT-2-CertValidfor7days: %[Message=Certificate expiration Notification. Certificate name: cucm.company.com.der Unit:tomcat-trust Type:own-cert Expiration][AppID=Cisco Certificate Monitor][ClusterID=][NodeID=cucm]: Alarm to indicate that Certificate has Expired or Expires in less than seven days AppID : Cisco Syslog Agent ClusterID :
NodeID : cucm
TimeStamp : Sun Oct 15 19:00:01 CDT 2017
CSR generation for Cisco Unified Communication Manager (CUCM)
- Log in to the OS admin page of your Cisco CUCM Publisher server.
- Generate NEW CSR.
- Navigate to Security > Certificate Management > Generate CSR.
- Select/enter the values in the table below and click Generate.
Certificate PurposeTomcatDistributionMulti-Server(SAN)Common NameRemove “-ms”Other DomainsAdd if any additional domains are required
Once the CSR has been generated, a Download CSR button will appear.
- Click Download CSR.
- Select Tomcat from the dropdown menu and click Download CSR.
- Send the output file to your Certificate Authority for signing.
- To install the Certificate navigate to Security > Certificate Management > Upload Certificate/Certificate chain.
Certificate PurposeTomcatUpload FileProvide the certificate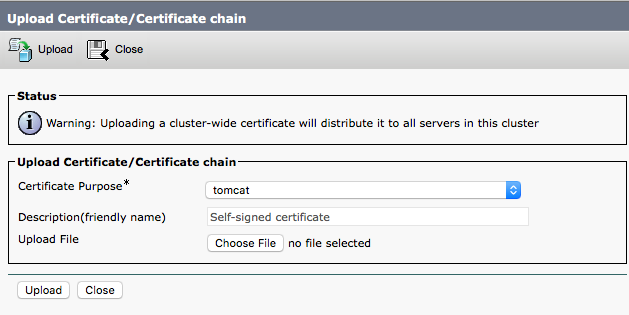
- Click Upload.
If you receive an error, you may need to upload the Root chain first. Root chain is already installed for the current certificate but could change at the renewal time. If Root chain must be uploaded, select tomcat-trust in the dropdown. - Restart Tomcat.
To make changes active, you must restart the Cisco Tomcat service on all cluster nodes. Don’t forget the IM & Presence servers as well, as they are part of your CUCM cluster starting from version 10.x.
The following step will impact all HTTP communications and will affect some services like system provisioning, Jabber login, Directory search, etc.
- Using an SSH client (putty, SecureCRT), log in to each server.
- Issue the following CLI command:
utils service restart Cisco Tomcat
CSR generation for Cisco Unified Communication IM & Presence
- Log in to the OS admin page of your IM&P server.
- Generate NEW CSR.
- Navigate to Security > Certificate Management > Generate CSR
- Select/enter the values in the table below and click Generate.
Certificate PurposeCup-xmppDistributionMulti-Server(SAN)Common NameRemove “-ms”Other DomainsAdd if any additional domains are required
Once the CSR has been generated, a Download CSR button will appear.
- Click Download CSR.
- Select Tomcat from the dropdown menu and click Download CSR.
- Send the output file to your Certificate Authority for signing.
- To install the Certificate navigate to Security > Certificate Management > Upload Certificate/Certificate chain.
Certificate PurposeCup-xmppUpload FileProvide the certificate
- Click Upload.
If you receive an error, you may need to upload the Root chain first. Root chain is already installed for the current certificate but could change at the renewal time. If Root chain must be uploaded, select cup-xmpp-trust in the dropdown. - Restart Cisco XCP Router service.
To make changes active, you must restart the Cisco XCP Router service on all IM&Presence server nodes. Restarting XCP router service will impact Jabber functionalities, so you may consider restarting this service after business hours.
CSR generation for Cisco Unity Connection
- Navigate to Security > Certificate Management > Generate CSR.
- Select/enter the values in the following table and click Generate.
Certificate PurposeTomcatDistributionMulti-Server(SAN)Common NameRemove “-ms”Other DomainsAdd if any additional domains are required
Once the CSR has been generated a Download CSR button will appear.
- Click Download CSR.
- Select Tomcat from the dropdown menu and click Download CSR.
- Send the output file to your Certificate Authority for signing.
- To install the Certificate navigate to Security > Certificate Management > Upload Certificate/Certificate chain.
Certificate PurposeTomcatUpload FileProvide the certificate
- Click Upload.
If you receive an error, you may need to upload the Root chain first. Root chain is already installed for the current certificate but could change at the renewal time. If Root chain must be uploaded, select tomcat-trust in the dropdown. - Restart Tomcat.
To make changes active, you must restart the Cisco Tomcat service.
The following step will impact all HTTP communications and will affect some services like system provisioning.
- Using an SSH client (putty, SecureCRT), log in to each server in the list.
- Issue the following CLI command:
utils service restart Cisco Tomcat
3. Cisco Jabber certificate renewal process for Cisco Expressway
IMPORTANT!
For Jabber Mobile and Remote Access (MRA) and Business to Business calls (B2B), it is mandatory to have a CA-signed certificate on the Expressway-Edge node. On the other hand, there is no such requirement for Expressway-Core. However, at ZIRO we recommend a CA-signed certificate be used on both Expressway servers to avoid “Cisco Jabber certificate not valid” errors.
Another requirement is to cross upload all Root and Intermediate certificates on both nodes for the Secure Traversal Zone to be active and communication between two Expressway nodes to work.
Each time you renew your certificates, do not forget to verify if there is a change on the Root or any of the Intermediate certificates. Upload all new chain certs in the Trusted Certificates section of the server.
CSR generation for Cisco Expressway-C
- Navigate to Maintenance > Security Certificates > Server Certificate > Generate CSR.
- In the Additional alternative names section, you don’t need to add anything.
- Fill in the rest of the fields.
- When done, select Generate CSR.
- Download the output file and submit it to your Certificate Authority for signing.
- Install Certificate: navigate to Maintenance > Security Certificates > Server Certificate > Upload new certificate
- Provide the certificate file and click Upload server certificate data.
IMPORTANT! Immediately after the upload, the web service will restart, this will cause all communication to drop.
- If you receive an error, you may need to upload the Root CA and Root chain first. Root CA and the chain is already installed for the current certificate but could change at the renewal time.
- If Root chain must be uploaded, navigate to Maintenance > Security Certificates > Trusted CA certificate.
- Provide the certificate file and click Append CA certificate.
CSR generation Cisco Expressway-E
- Navigate to Maintenance > Security Certificates > Server Certificate > Generate CSR.
- In the Additional alternative names section, add all domains that have been used by Jabber (external and internal). You will need to add a common cluster name of the Expressway nodes if you have a cluster deployment, or if you plan to deploy an Expressway cluster in the future.
- Make sure to add the names of the Phone Security Profiles in CUCM that are configured for encrypted TLS and are used for devices requiring remote access (applies only for CUCM in Mixed mode).
- When done, select Generate CSR.
- Download the output file and submit it to your Certificate Authority for signing.
- Install Certificate: navigate to Maintenance > Security Certificates > Server Certificate > Upload new certificate
- Provide the certificate file and click Upload server certificate data.
IMPORTANT! Immediately after the upload, the web service will restart, this will cause all communication to drop.
- If you receive an error, you may need to upload the Root CA and Root chain first. Root CA and the chain is already installed for the current certificate but could change at the renewal time.
- If Root chain must be uploaded, navigate to Maintenance > Security Certificates > Trusted CA certificate.
- Provide the certificate file and click Append CA certificate.
Secure Traversal Test
Once you upload newly signed certificates and Root as well as Intermediate certificates in the Trust CA certificates store, you should run a small test:
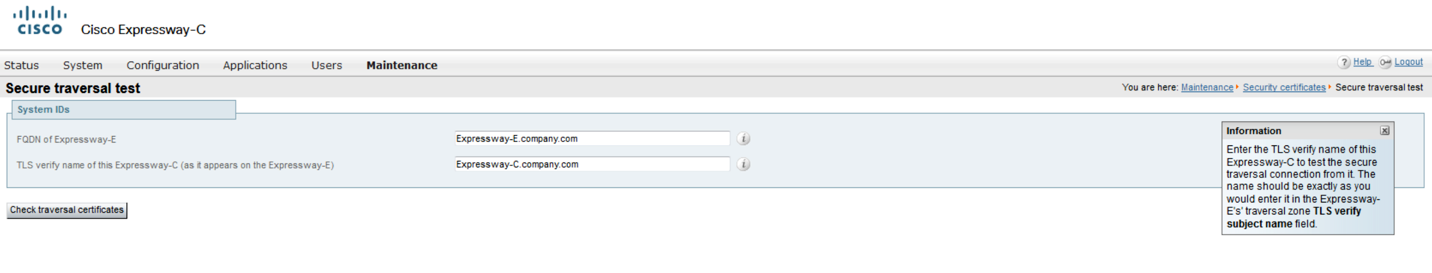
- Go to Expressway-C > Maintenance > Security certificates > Secure traversal test
- In the first field, enter the FQDN of an Expressway-E to test the secure traversal connection to it. The FQDN should be exactly as you would enter it in the secure traversal zone’s peer list.
- In the second field, enter the TLS verify name of the Expressway-C to test its secure traversal connection. The name should be exactly as you would enter it in the Expressway-E traversal zone TLS verify subject name field.
- Result returned after the test should be Success!
Summary
Managing Cisco Jabber certificate validation and verification can be challenging. The certification process outlined above not only provides easier ways to verify and validate certificates but also provides step-by-step guidance to generate new CSRs based on your environment.
If you are interested in learning more about Cisco Jabber or require assistance with verifying, validating, and renewing your Cisco Jabber certificate, please reach out to our Professional Services Team.
You can also learn more about how we remove many other Cisco UC hassles by exploring our Managed Services.
—
Editor’s Note: This post was originally published as a three-part series in November 2017.
Ready to take your unified communications from headache to hassle-free?
No throwing darts at proposals or contracts. No battling through the back-end. No nonsense, no run-around.



