Microsoft Secure LDAP Security Update for Cisco UC Systems and SMACS
Over the coming months, Microsoft will be publishing security updates related to Advisory ADV190023 that will significantly affect how LDAP can be used in a Microsoft Active Directory (AD) environment. In the first round of security patches scheduled for March 2020, logging will be enabled by default for insecure LDAP connections. In the second half of 2020 (so no earlier than July), insecure LDAP communications will be blocked. This will affect all external systems that make use of LDAP to synchronize and authenticate users.
We know that the timeline presented above runs counter to some information provided by Microsoft and other third parties. In order to ensure the accuracy of the information we provide to our clients, we opened a support case with Microsoft to validate the exact behavior of the patches. They have confirmed the timeline we present to you as the most recent information on this advisory, which has seen a number of revisions since its inception last August. We strongly recommend taking immediate action to address this situation despite this extended timeline.
At Stack8, we support, manage and develop applications that make it simple and easy for our clients to use unified communications technology. In this context, we have investigated this issue, the impact on our client’s unified communications infrastructure, and the products we develop for our clients. We present our recommendations on remediation, based on this investigation, below.
While enabling secure communications with LDAP servers is a clear security best practice, being able to implement it depends on specific AD configuration that is not present in every environment. Because of this, many installations of Cisco UC products, as well as our own SMACS UC provisioning tool, do not make use of secure LDAP communications.
Addressing this issue is a three-stage process:
- Validate that your AD servers support secure LDAP.
- Enable it if they do not.
- Reconfigure applications using LDAP services to use secure communications methods with your servers.
Validate that your AD infrastructure supports secure LDAP
We based this guidance on the following website, which explains how to validate LDAPS on a domain controller:
On an AD DS server, use: Start > Run and execute ldp.exe (this can also be installed on any Windows 10 workstation using the RSAT tools and/or optional Windows 10 administration features).
Connection > Connect> Specify your AD server by FQDN and port 636, Check the SSL checkbox
If you get a “Cannot open connection” response, then your server is not listening for SSL or is unreachable. If you connect, then validate the log in messages from the LDP tool for the following information related to the connection security:
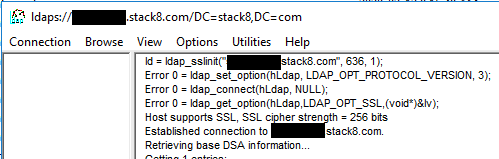
Enable LDAPS
If you are not presently able to connect to your AD DS server using LDAPS, then you probably do not have the necessary certificate and key installed on the server to support a TLS connection. While we cannot provide detailed guidance on AD DS services and recommend that you rely on either senior internal resources or the guidance of a trusted and experienced Microsoft partner, the easiest way to achieve this for all your servers may be through the deployment of the AD CA role on a dedicated server. This will allow all of your servers to receive certificates issued by a central CA server.
Reconfigure your servers
Cisco UC
Cisco provides detailed information on reconfiguring your servers in this field notice Secure LDAP Mandatory for Active Directory Connections. Be sure to note that there are two different locations where the server can be configured in CUCM.
SMACS
In the LDAP Management section of the Admin settings, ensure that your LDAP server is configured with the name and not the IP address of the LDAP server. Change the connection to use LDAPS; you will notice the port change from 389 to 636. Save the changes.
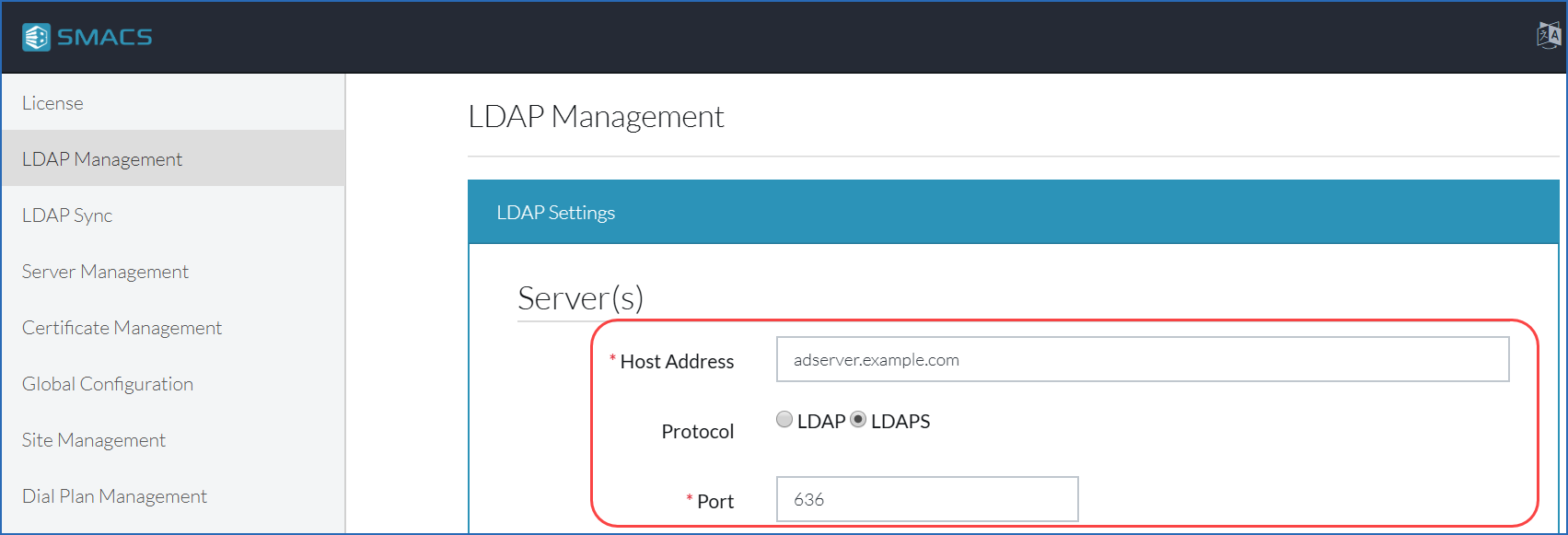
If you experience issues with this change, then revert back to the original values and submit a ticket to our support team.
UC Support
If understanding and implementing the required changes to support the LDAP security improvements is challenging for your team, perhaps you could benefit from our Stack8 managed services offering. Please contact us here; our team is ready to make it simple and easy for you to deliver on your promises to your clients.
Technical Background and Details
The March patch release will enable additional event messages warning administrators of insecure connection behavior. However, it will not block insecure connections to an LDAP server. This will be achieved by changing the LdapEnforceChannelBinding value to 1, as described in this article. The future update, expected July or later of this year, will then block these connections by changing the LDAPServerIntegrity value to 2.
Ready to take your unified communications from headache to hassle-free?
No throwing darts at proposals or contracts. No battling through the back-end. No nonsense, no run-around.



