Many organizations struggle to secure large networks designed before internal network segmentation and security became a primary concern. I’ll show you how to use VRF segmentation to secure new network deployments as well as retrofits.
TL;DR
- We have helped many organizations secure their network with VRF segmentation.
- With VRF, network paths can be automatically segmented without needing multiple devices. This increases security as a result.
- I’ll walk you through a typical scenario to show how we set up VRF network segmentation for our customers.
- ZIRO can help you set up a VRF or work through your own network architecture.
I know how hard it is to retrofit security into a network design while:
- Avoiding changing server configurations
- Minimizing downtime and impact
- Maintaining performance within existing network segments
- Progressively phasing in security rules.
Thankfully, this doesn’t need to be such a hassle. At ZIRO, we have successfully implemented solutions with VRF segmentation in both large managed VPN environments and corporate networks with multiple facilities. Let me show you how we do it.
What is a Network VRF?
When talking about VRF in networking, we’re referring to a technology that allows a network device to maintain multiple distinct routing tables on the same switch or router. Because the internal network segmentation is happening automatically, a VRF can increase security and might even eliminate the need for encryption or authentication for certain organizations.
Our Approach to VRF Segmentation
The Scenario
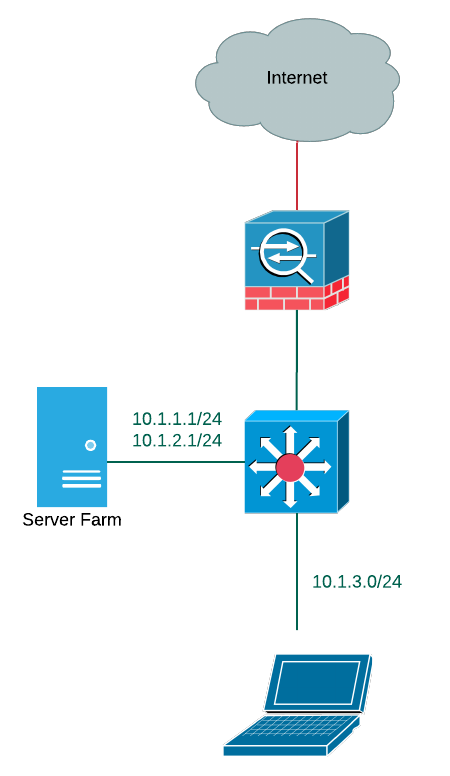
Let’s used a simplified example of an organization that has two server networks (10.1.1.0/24 and 10.1.2.0/24) that need to communicate with each other at a line rate. Users are in a network segment in 10.1.3.0/24. After a recent audit, the organization has discovered several issues:
- There is a lack of internal network segmentation,
- They have exposed all users to the administrative interfaces of the servers.
- There are many difficult-to-patch applications.
The Process
We could introduce a next-generation firewall with IPS capabilities in response to these legitimate concerns. However, there are a wide variety of servers, applications, and appliances in the two server networks, and their interaction with the user network isn’t fully understood. Some of them are licensed based on their IP address and the server administrators are not eager to change the network design or configuration.
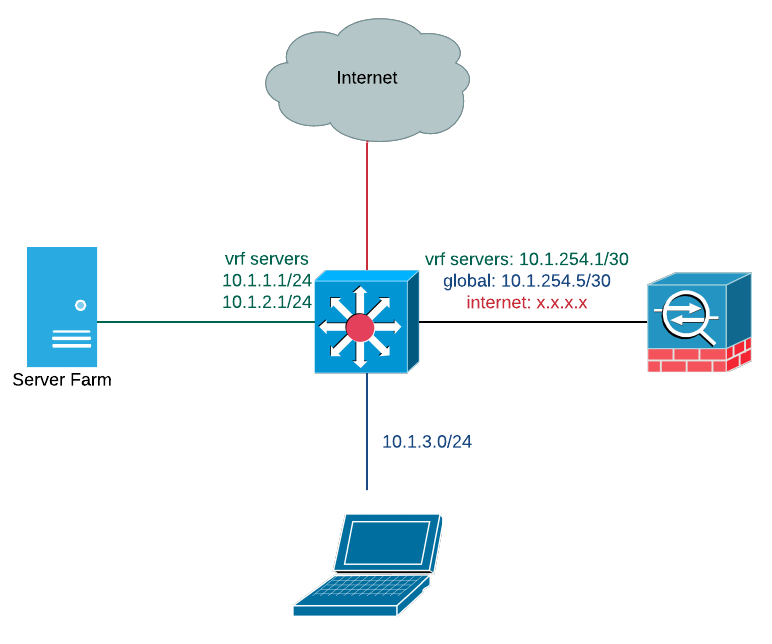
To separate the users from the servers, we will create a new VRF routing table on the core switch. Devices in different VRFs can’t communicate with each other. We will place the two server networks inside a new VRF called servers. The gateway IP addresses will remain on the switch and there will be no impact on the speed of communications between servers in different subnets. We will leave the users in the global routing table in this example.
We will also create two new /30 networks to connect the two network segments to a next-generation firewall. The firewall can be either physical or virtual. We typically run OSPF on the firewalls and core switch to exchange routing information between the devices. While there isn’t much of a need in this simple example, we use this for redundancy in most of our designs. The firewall continues to terminate the Internet connection as it did before the change.
With these changes made, traffic from users to the servers will now pass through the firewall. We would typically start in monitoring mode with a set of rules permitting all traffic so we can start to analyze the traffic between the users and servers. We progressively build out rules for desirable traffic until we can remove the permit-all rules.
The Benefits of VRF Segmentation
This is a powerful solution to help address internal network segmentation needs while minimizing changes and maintaining performance. The groundwork is all done in advance, allowing the firewall to be fully deployed. Then, during a brief maintenance window, you change the VRF on the interfaces and change the traffic flow to pass through the firewall.
Building out from these techniques we have:
- Used multiple firewall devices with different route costs for high availability
- We have extended from these principles to build out redundancy with multiple firewalls at different sites.
- We have extended segments between different WAN sites so that server traffic between two data centers will flow within the VRF between the two sites.
- In a large managed VPN environment with centralized services and internet access for content filtering, we have traffic landing on VPN routers inside a VRF, from their traffic flows through a central firewall to access either central resources or the internet.
- Some of these resources are remote services accessed via another VPN. Rather than deploy additional hardware for this VPN, we have placed these tunnels in another VRF, allowing traffic to arrive on the VPN router, pass through the central firewall/IPS for inspection, and filter before returning to the same VPN router to reach the remote service.
If you have questions about VRF segmentation or are looking for help working through your own network architecture, we are here to help!
Contact us here or call +1-844-940-1600.
_
Editor’s Note: We originally published this post on June 6, 2016.
Ready to take your unified communications from headache to hassle-free?
No throwing darts at proposals or contracts. No battling through the back-end. No nonsense, no run-around.



